Identity Verification in the Era of Gen AI Deepfakes
Thanks to the rapid development and dissemination of generative AI tools, deepfakes have gone from being a curiosity and entertaining gimmick to being a real problem — especially in the field of identity verification. While in the past, creating a deepfake required expertise in data science and photo (or video) manipulation techniques, today anyone can create a deepfake with little more than an internet connection and source material.
If that sounds like a security and compliance nightmare, you’re not wrong. These are exciting and somewhat scary times. But the good news is that with the right technology and strategy in place, it’s possible for your business to detect deepfakes and prevent them from skirting through your IDV measures.
Below, we take a closer look at what deepfakes are and how fraudsters try to use them to get around identity verification. We also offer advice you can use to craft an IDV strategy capable of stopping deepfakes in their tracks.
What are deepfakes?
A deepfake is a digitally manipulated photo or video, in which a person’s likeness is replaced with someone else’s likeness. They are also sometimes known as synthetic images.
While “deepfake” traditionally refers to photos and videos of individuals, the term can also be used more broadly to refer to synthetic or manipulated IDs, such as driver’s licenses, passports, and ID cards, and documents, such as bank statements, pay stubs, Social Security cards, birth and death certificates, and more.


How do deepfakes work?
Fraudsters may use a variety of techniques to generate a deepfake, but two common methods are face morphing and face swapping.
With face morphing, a fraudster blends together the faces of two different individuals in order to create a third, fake image that resembles the two source photos.
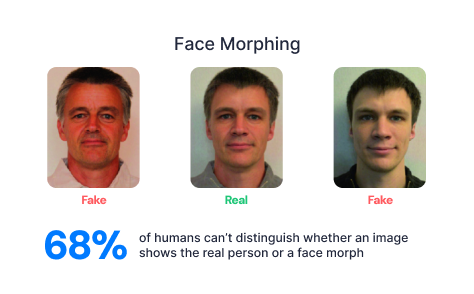
With face swapping, a fraudster also starts with a photo of two different individuals. But instead of blending the faces together, they transpose the face of one individual on top of the photo of the second individual.

While it’s possible to achieve both of these effects through manual manipulation (for example, in a tool like Photoshop), they are increasingly achieved through the use of artificial intelligence (AI), machine learning (ML), and generative AI.
How Fraudsters Use Deepfakes to Skirt IDV
Once a fraudster has created a deepfake, they can use those fake photos or videos to try and bypass ID verification and selfie verification measures. They typically do this through presentation attacks and injection attacks, each of which works slightly differently.
Presentation Attacks
A presentation attack occurs when a fraudster tries to get around biometric or camera-based verification by presenting a false likeness to the camera. According to research conducted by Gartner, presentation attacks are the most common way that fraudsters attempt to use deepfakes.
Typically, presentation attacks will look something like this:
- The fraudster creates a deepfake, such as a fake selfie or fraudulent ID.
- The fraudster then prints out a high-definition copy of the selfie or ID. Alternatively, they may simply display the deepfake on a second device, like a laptop, smartphone, or tablet screen.
- When they are prompted to capture a selfie or photo of their ID during the verification process, they hold the printed deepfake (or digital copy) up to the camera.
If the identity verification solution does not recognize the deepfake for what it is, then the fraudster has successfully worked around the verification process.
Injection Attacks
An injection attack occurs when a fraudster uploads (i.e., injects) a previously-generated deepfake instead of capturing a selfie or photo in real time. Gartner research shows that, while injection attacks account for a smaller percentage of total deepfake attacks, the total number of estimated injection attacks increased by 200% in 2023.
A typical injection attack usually looks something like this:
- The bad actor creates a deepfake, such as an ID or selfie, and saves the deepfake in the appropriate file format on their device.
- When prompted to capture a selfie or photo of their ID during the verification process, the fraudster then uses a tool like an emulator or virtual camera to bypass the physical, legitimate camera on their device.
- Once the physical camera is bypassed, the bad actor uploads the previously generated deepfake.
If the IDV solution does not detect this false data, then the fraudster has successfully passed their deepfake off as a legitimate camera capture.
How to Detect Deepfakes During IDV
At the end of the day, there’s no single foolproof way to detect and prevent 100 percent of deepfakes 100 percent of the time. That’s why, here at Incode, we emphasize the importance of leveraging multiple layers of defense within your IDV strategy.
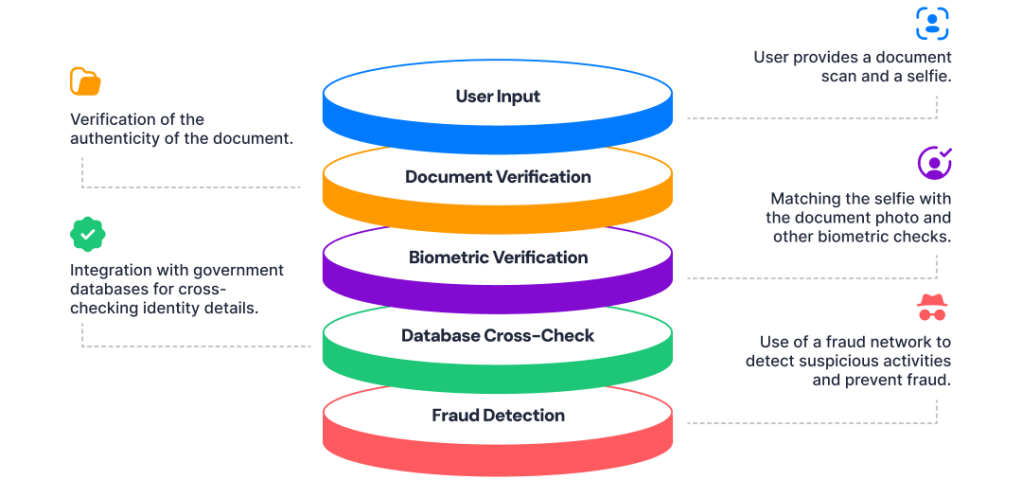
Below, we highlight some of the measures that we have built into our system to help you detect and stop deepfakes:
Selfie Liveness Checks
Incode’s platform leverages numerous passive liveness checks that empower it to differentiate between a living person and a spoof — digital or physical — that a fraudster might try to use to trick selfie verification.
Liveness detection uses multi-frame capture and device hardware like TrueDepth cameras to:
- Capture and analyze spatial data and micro-movements
- Ensure the presence of a live person
- And detect subtle biometric cues associated with deepfakes
We categorize these multitude of checks into 3 buckets:
- Digital Spoof Check, which looks for signs of digital spoofing typical of face morphs and face swaps commonly used in creating deepfakes
- Physical Spoof Check, which looks for signs of physical spoofing such as printouts, replayed images or video, and physical masks
- Face Evasion Check, which detects the presence of unexpected extreme facial expressions which are commonly found in some deepfakes
Additional checks analyze the textures, patterns, glare, shadows, and field of depth contained within an image to ensure they match with what is expected.
ID Liveness Checks
Of course, fraudsters don’t just use deepfakes to create fake selfies. The technology can also be used to generate fake documents and IDs. Incode’s ID liveness checks are specifically designed to differentiate between real and falsified IDs.
Our Screen ID Liveness Check, for example, analyzes an image of an uploaded ID to determine whether it is a photo of a physical ID or a photo of an ID displayed on the screen of a secondary device — such as a phone or tablet.
Our Paper ID Liveness Check, meanwhile, analyzes the material composition of the image in order to differentiate between a legitimate ID and a physical counterfeit. The presence (or lack) of glares and security features (like holograms, foils, and microtextures) all aid in this analysis.
Facial Recognition
AI-powered tech analyzes user behavior & biometric data to detect spoofs and ensure the right person is verified. Facial Recognition tech goes beyond traditional methods, using deep neural networks to:
- Compare live captures with stored biometric data
- Ensure precision in real-world conditions and diverse populations
Once an ID and selfie have been captured, biometric checks allow us to compare the two photos to determine whether the faces in each match, and to what degree they match using. It also ensures that the person going through the IDV process is the actual owner of the ID, which is a particularly helpful backstop against stolen or lost IDs.
If the checks reveal too low of a match score, it may point to a crude attempt at a face swap or face morph. If the checks reveal too high of a match score — such as an unlikely 100 percent match — it may point to a sophisticated deepfake.
System of Record (SoR) Validation
Incode uses exclusive connections with government identity issues to perform ID and biometric verifications.
Comparing enrollee data against secure, authoritative government sources. This surpassing traditional methods in accuracy for unrivaled fraud prevention.
By comparing the information contained within an ID as well as the facial biometric data captured through the selfie, against the information contained in authoritative government databases, Incode offers an additional layer of defense against fraudsters.
These partnerships extend to other governmental data sources, commercial registrars, and third-party data providers like telcos and credit bureaus.

Incode’s Fraud Network
Incode has validated hundreds of millions of identities, using big data to enrich our network with millions of user interactions – to identify and prevent fraudulent behavior.
Advanced AI powers the Incode Fraud Network – a predictive and preventive approach to fraud:
- Our proprietary vector database stops threats in real-time by comparing incoming facial data with flagged fraud vectors
- Pattern recognition cross-references risk signals against a database of known fraud indicators
- Additional fraud signals verify the legitimacy of the device itself and flag network anomalies like mis-matched IP addresses and VPN usage
The presence of one or multiple suspicious signals could be enough to trigger enhanced due diligence, protecting your business from fraud and deterring would be fraudsters to target your business in the future.
Robust Platform Security
Customers integrating Incode Verify benefit from advanced security measures that can detect the use of web hooks, roots, emulators, unauthorized virtual cameras, and unexpected software signatures during the capture process to prevent avenues for media injection.
Protect your business against deepfake fraud with Incode
No single technology is 100 percent effective at detecting deepfakes. That’s what makes a proven, multi-layered approach to identity verification, like the one offered by Incode’s platform, so important. Even if a fraudster is able to make it through one or two layers of your defense, the chances of them making it through all of them are slim-to-none.
Want to learn more about how Incode’s platform can help you build an IDV strategy capable of detecting and stopping deepfakes? Get in touch with an Incode Identity Consultant, or request a free demo today.
