Authentication.
Your biometric identity is the only authenticator you can’t lose. Close security gaps with biometric authentication to protect account logins, password resets, and high-risk transactions.
Top companies switch to Incode for our proven impact on fraud protection and growth

99.9%
Accuracy in authenticating identities
1.5s
To authenticate with a selfie for secure access
4x
Better fraud prevention compared to industry average
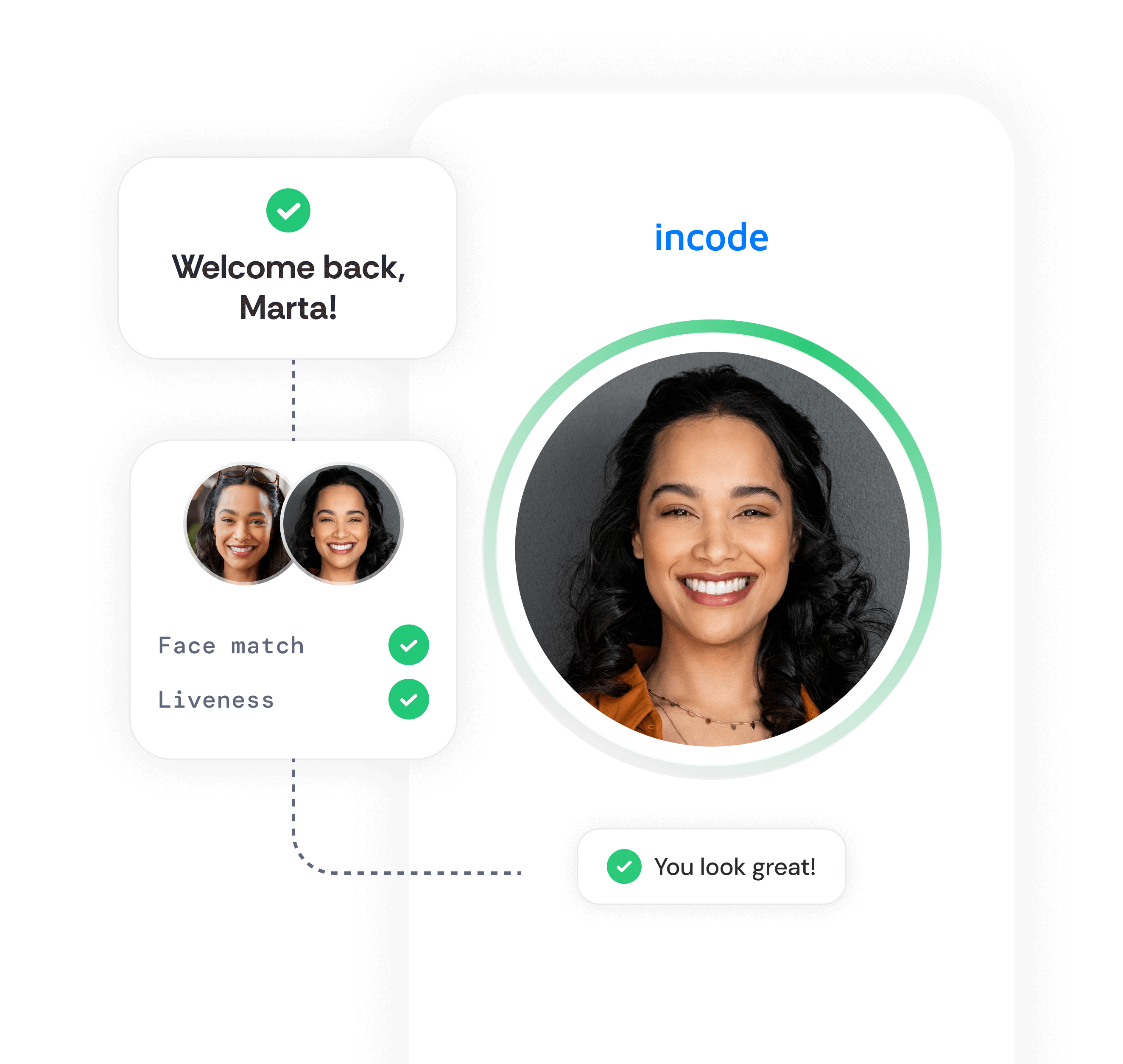
Enhance security with face factor authentication.
After a one-time identity verification to match the valid ID document with a live photo capture, users can authenticate on any device with a simple selfie.
Empowering users to authenticate in the most intuitive and secure way possible
Unspoofable facial biometrics
Verified and securely stored digital identities make device spoofing and credential theft nearly impossible for fraudsters.
Detect more fraud at every interaction
Incode’s face authentication detects 99.9% of fraud, eliminating security gaps at any stage of the user lifecycle.
Offer the best user experience
Face factor authentication takes 1.5 seconds to complete using any device, providing fast and frustration-free security for users.
Face authentication is the key to secure, recurring identity verification
Traditional password- and device-based security factors without verifiable biometric factors are increasingly compromised by social engineering attacks
Face Authentication vs. Face Unlock on smartphones
Face Factor Authentication (FFA) and smartphones’ Face Unlock features serve different purposes.

Face ID and face unlock
Enhances personal device convenience, but the local storage of biometrics creates significant security risks if the device is compromised.
FFA
Stores authorized users’ biometrics securely in the cloud, preventing access by unauthorized persons even when passwords or the device itself are compromised.

Biometric authentication to secure your business
Protect critical transactions with a safely stored biometric authentication layer that powers friction-free security.
Secure high-risk moments
Users authenticate before authorizing transactions, submitting approvals, and sharing confidential documents.
Protected credential recovery
Enable users to restore account access with self-serve portals protected by face authentication.
Easy step-up verification
Face biometrics allow quick and easy step-up verification to secure any business trasnaction with minimal friction compared to device tokens and OTPs.




