Why Incode’s KYB Business Verification is a Must for Any Organization
When governments and institutions discuss compliance with Know Your Customer (KYC) and Anti-Money Laundering (AML) laws and regulations, they also discuss the need to comply with “Know Your Business (KYB)” laws and regulations.
- What is Know Your Business?
- What is wrong with older KYB offerings?
- What is the revolutionary way in which Incode’s customers are complying with KYB regulations today?
What is KYB?
KYB is one of many tests that governments and businesses use to detect illegal financial activity. Specifically, KYB confirms that a purported business is a registered entity, and also checks the business against various watchlists. If you are contracting with a particular business, KYB ensures the business is not involved in fraud, criminal activity, money laundering, or terrorism.
While KYC verifies the identities of individuals, KYB verifies the identities of businesses. KYB also includes identity verification of the ultimate beneficial owners (UBOs), legal representatives, and other authorized individuals associated with a business.
Therefore, your complete identity verification solution should include both KYC and KYB. Adopting KYC without considering KYB puts your company at risk for both fraudulent activities from questionable businesses, and government fines for facilitating illegal activity by questionable businesses.
A thorough KYB check consists of the following steps:
- Capturing all relevant information related to the business.
- Capturing all relevant information related to the UBO(s).
- Completing business and UBO/authorized individual checks of the captured data.
KYB is a valuable tool in the arsenal of businesses that wish to comply with anti-money laundering laws, and of governments that want to eliminate terrorist and criminal activity.
That is, KYB is a valuable tool…if it works.
Why outmoded KYB offerings don’t protect businesses and governments
All the necessary KYB data captures and checks can be time-consuming, especially if significant portions of the KYB process are performed manually.
Manual business verification solutions suffer from the same problems as manual individual verification solutions. Incode’s e-book “Three Problems With Manual Verification” (discussed here) outlines some of these problems.
Manual verification/authentication compromises accuracy.
- Users who must enter submissions (faces, ID documents, bank account information) manually may not capture them correctly, unlike AI/ML solutions that automatically capture submissions only when they meet quality criteria.
- Users who must capture faces and ID documents manually may not capture them correctly, unlike AI/ML solutions that automatically capture faces and ID documents only when they meet quality criteria.
- Similarly, users who must manually enter information from a bank statement or Letter of Authorization (LOA) may introduce typographical errors that delay verification, unlike AI/ML solutions that accurately read the necessary information from a bank statement or LOA without requiring any user interaction that introduces error.
- Manual reviewers may not be equipped to identify fraudulent submissions such as fake facial images, and manual reviewers cannot constantly improve as automated AI/ML models do.
- Similarly, manual reviewers may make mistakes when comparing all the submitted information (for example, the name on a bank statement and the name on an LOA). AI/ML solutions instantly catch discrepancies that fatigued humans may miss.
- Solutions that require companies to manually re-check business status expose the business to fraud if those checks are not performed. Automatic continuous verification solutions report changes to business status instantly, allowing immediate responses to bankruptcies, sanctions, and other negative events.
Manual verification/authentication takes time.
- Solutions that depend upon active liveness detection, where the person must manually move their face to confirm liveness, are cumbersome, cause friction, and delay submissions.
- Solutions that require users to manually enter data also delay submissions. Contrast this with solutions that automatically capture data in real-time, allowing rapid submissions.
- Solutions that depend upon manual reviewers suffer when a flood of submissions delays results, and the manual reviewers must work through a backlog that may take hours or days to complete. Automated solutions are scalable when workload increases, and peaks in submissions are addressed by simply adding more processing servers. This allows automated solutions to always provide real-time results.
- Slow and difficult procedures may result in user abandonment of the process, reducing its effectiveness.
Manual verification/authentication compromises privacy.
- Submissions that require manual review expose the personally identifiable information of individuals. Manual reviewers can see the most private details of a business and its key people, including full names, addresses, government identification numbers, bank account numbers, and detailed financial information.
- Most worrisome, the use of manual verifiers to perform a KYB process may result in theft of personal data to facilitate the commission of additional crimes. Do you want a supposed crime prevention solution that causes even more crime?
These older solutions fail to protect businesses and allow criminals to hide behind false identities and shell businesses. A better solution is needed.
How can you implement easy-to-use KYB checks that ensure compliance and provide rapid results?
Incode’s revolutionary KYB Business Verification offering
Incode customers are already conducting automated, easy-to-use KYB checks with a better solution. As KYB becomes more important, Incode is receiving more requests for our revolutionary KYB solution that eliminates the problems with older solutions and provides the same benefits as our other identity verification solutions.
Incode’s KYB Business Verification offers the necessary automation and approves business checks in real time. Because of the problems with manual identity verification, KYB Business Verification automates many parts of the process, including face capture, ID document capture, capture of other documents such as bank statements, and other critical steps.
In addition to offering more automation than other KYB solutions, KYB Business Verification provides:
- Accurate, real time, and privacy-protecting Incode-developed AI/ML algorithms. These core algorithms are Incode-developed, not dependent on third parties, and allow Incode to manage and continuously improve key aspects of the KYB solution, including:
- Capture, passive liveness detection, and matching of faces using Incode-developed, NIST-tested, and iBeta-conforming face processing algorithms.
- Capture, liveness detection, and data extraction from ID documents using Incode-developed ID document processing algorithms.
- Capture, document classification, and data extraction of ID documents, bank statements, LOAs, and other textual documents using Incode-developed algorithms.
- Accurate, real time, and privacy-protecting checks of all data associated with a business, including:
- The business’ registered name.
- Deliverability and verification of the business’ registered and operating address.
- The business’ Employer Identification Number (EIN), or an equivalent number used to verify a business’s unique identity.
- The business registration status, as maintained by the relevant government agency (in the United States, state-level Secretaries of State).
- Business bank account information.
- Other business documents.
- Accurate, real time, and privacy-protecting checks of the business against relevant watchlists such as the following U.S. Government watchlists:
- Entity List (EL), Bureau of Industry and Security.
- Denied Persons List (DPL), Bureau of Industry and Security.
- Military End User (MEU), Bureau of Industry and Security.
- Unverified List (UVL), Bureau of Industry and Security.
- ITAR Debarred (DTC), State Department.
- Nonproliferation Sanctions (ISN), State Department.
- Capta List (CAP), Treasury Department.
- Foreign Sanctions Evaders (FSE), Treasury Department.
- Non-SDN Menu-Based Sanctions (NS-MBS), Treasury Department.
- Non-SDN Iranian Sanctions (NS-ISA), Treasury Department.
- Specially Designated Nationals (SDN), Treasury Department.
- Sectoral Sanctions Identifications List (SSI), Treasury Department.
- Non-SDN Chinese Military-Industrial Complex Companies List (CMIC), Treasury Department.
Logging and presentation of KYB session results on the Incode Omni dashboard, including the results of all the individual and business checks showing verification of identities and results of watchlist searches.
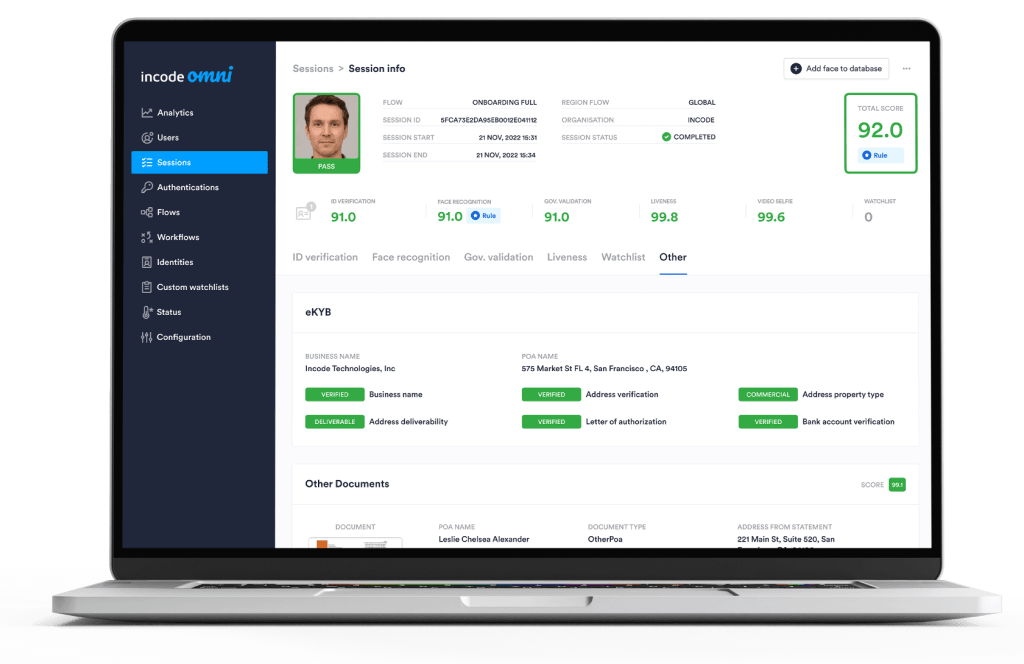
- Real time results to confirm or deny the authenticity of businesses and UBOs as quickly as possible, letting authorized businesses conduct business now while preventing unauthorized businesses from damaging your company.
- Continuous authentication of businesses in case their statuses change (bankruptcy, sanctions).
- Post-verification authentication of critical transactions with biometrics, such as changes to key individuals, registered business addresses, or bank account information.
- Protection of financial institutions and other regulated businesses from AML losses and government fines for non-compliance.
To see an example of KYB Business Verification use, watch the video below.
To read more about KYB Business Verification, download this data sheet.
If you are ready to join the KYB revolution, request a demonstration of KYB Business Verification below.
