Workforce.
Protect your help desk from social engineering by enhancing your IAM with real-world biometric authentication for employees.
Top companies switch to Incode for our proven impact on fraud protection and growth

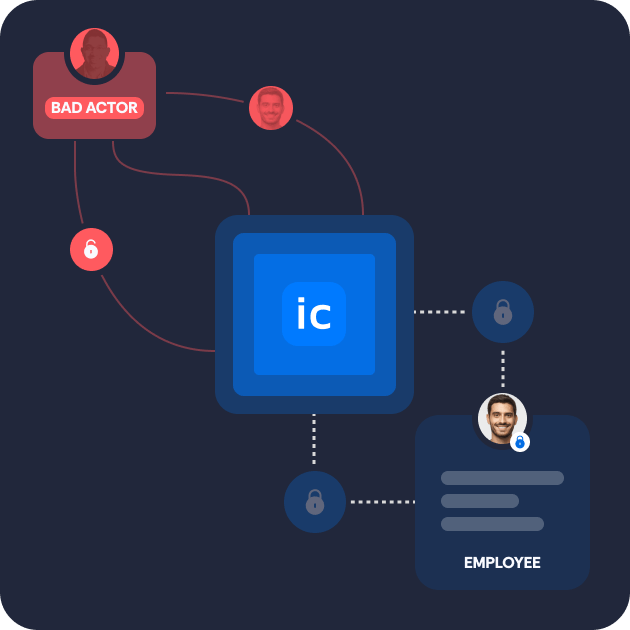
Fraudsters don’t crack MFAs, OTPs and passwords – they just go around them
Fraudsters use social engineering techniques to impersonate employees in distress, tricking IT support into resetting credentials. With advanced AI and deepfake tools, these attacks can be automated while becoming increasingly convincing.
Of organizations experienced an identity based fraud attack in 2023
Of organizations experienced an identity based fraud attack in 2023

All three scenarios represent an open back door to enterprise security protocols
Traditional MFA
Easily compromised, prone to phishing, and at risk when devices are compromised.
Device-bound factors
Can be bypassed by account recovery requests claiming to have lost the device.
Security questions
Time-consuming for help desks and users alike, and highly prone to social engineering.
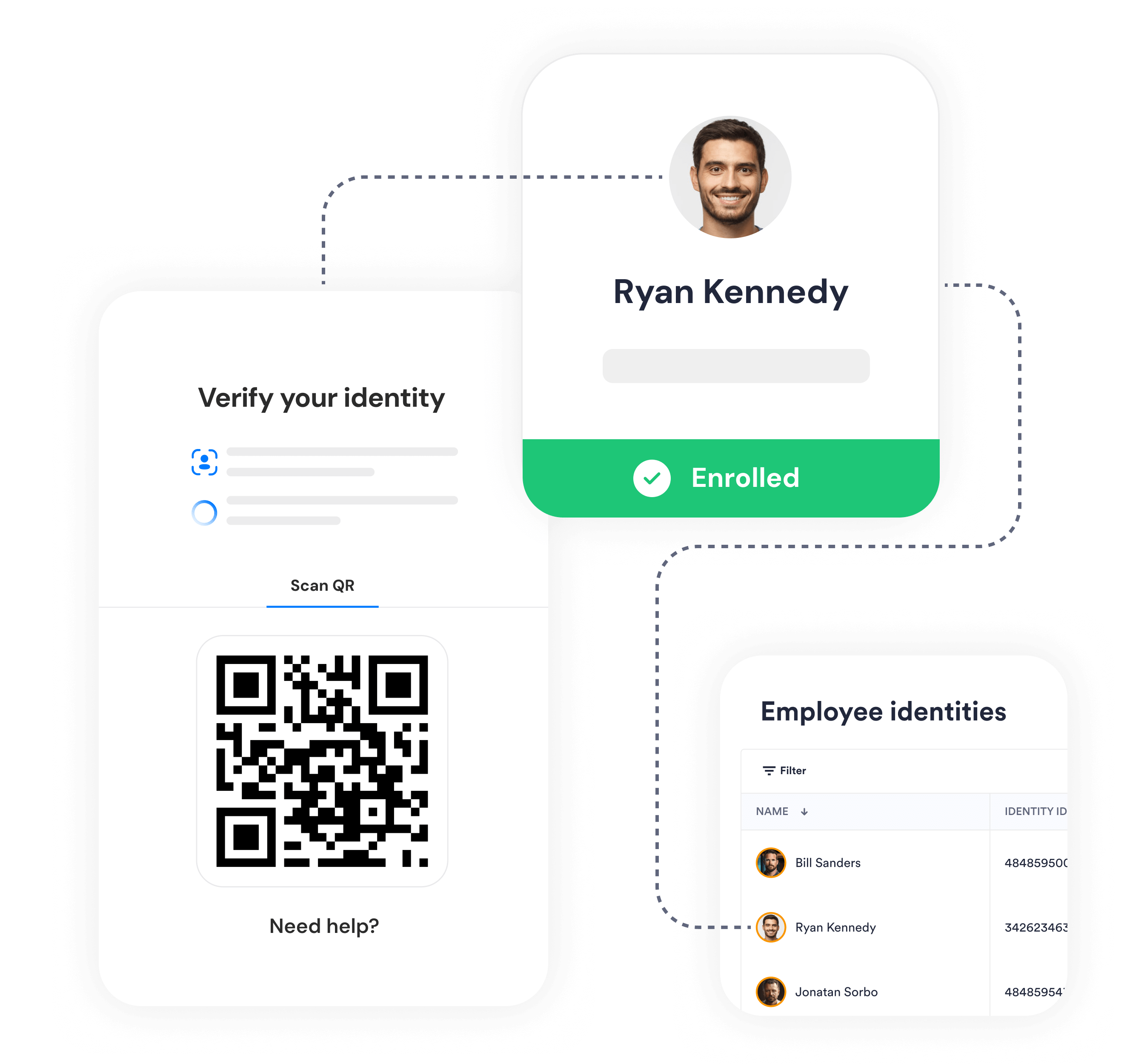
Enhance identity access management with a tamper-proof security layer
Here’s how it works
Here’s how it works
Fortify enterprise security and free up help desk capacity
Security
Augment enterprise security with face factor authentication (FFA) and close the back door to social engineering

User Experience
Employees authenticate in seconds with just a selfie, maintaining productivity with minimal friction

Cost Efficiency
Automate upwards of 50% of help desk tickets with self-serve portals
The Incode Advantage
With a strong grounding in AI-driven identity verification, Incode is the definitive partner in verifying employee identities for enterprise security.
Verified employee identities are fundamental to overall enterprise security
Secure mobile and remote access
Enable secure access to critical applications from any device and protect remote workers from getting locked out.
Safeguard financial transactions
Require authentication for high-risk payments to prevent possible fraud attack angles.
Mission-critical systems protection
Biometric step-up authentications put a stop to fraud, even if high-clearance employee accounts are compromised.
Enhance your IAM with an unspoofable biometric authenticator
Incode Workforce integrates with your existing IAM and ITSM systems in under 1 hour, and without a single line of code required.



