Building a Resilient Hiring Pipeline: Best Practices for Security
Today, the recruitment process has become a critical attack vector for identity fraud.
In our previous blog posts, The New Threat Surface: How Hiring Became a Vector for Attack and Anatomy of a Modern Candidate Fraud Attempt, we explore real-life examples of candidate fraud and break down common tactics used to deceive hiring teams, showing how fraudulent schemes often follow a repeatable, recognizable pattern.
AI-powered bots, synthetic IDs, and deepfakes are increasingly deployed to exploit vulnerabilities in hiring workflows that were never designed with security as the first priority. In today’s blog, we detail best practices for building a resilient hiring pipeline so your organization can stay ahead of evolving threats.
Why Traditional Hiring Workflows Can’t Catch Candidate Fraud
Recognizing how and why these candidate fraud schemes bypass traditional safeguards is the essential first step toward building stronger defenses.
1. Background checks come too late and trust candidate-provided data.
Many employers rely on background screenings (criminal checks, employment verification, etc.) as a safety net. But as Gartner observes, “traditional employment verifications and background checks are ill-equipped to uncover fraud in the recruiting process, as they occur in later stages of hiring and rely on candidate-provided identity data.”
In other words, if an applicant has built their entire identity on fraudulent or stolen information, a background check will simply confirm those false details (or at best, not flag anything amiss). These checks might catch a fake degree or a criminal record, but they won’t tell you if the person behind the resume isn’t real. By the time such checks are run (often after a conditional offer), the impostor is already deep into the process.
2. Resume screening and interviews focus on skills—not identity.
Traditional hiring funnels emphasize assessing a candidate’s experience, skills, and cultural fit. Recruiters and hiring managers are experts at evaluating resumes and conducting interviews, but they are not trained to authenticate identities or spot sophisticated deception. If a candidate can intelligently discuss projects and answer technical questions (perhaps with someone feeding them answers, or using AI assistance), interviewers may have little reason to suspect fraud.
Technical interviews can be gamed by proxies—e.g. a stand-in who pretends to be the candidate (a scenario that tools in place today rarely check for). Especially in remote hiring, an interviewer might never meet the person in real life until after they’re hired. A startling example was documented at one company where a candidate aced the video interviews and was hired, but a completely different individual showed up on the first day in their place. HR and Legal only caught on because the in-person appearance was so clearly a mismatch; had the job been fully remote, the swap might have gone unnoticed longer.
3. Lack of real-time verification during virtual interviews.
Most video conferencing platforms used for interviews do not have built-in identity verification. Recruiters typically don’t ask candidates mid-interview to show ID or prove liveness (and doing so could be awkward without proper tools and policies). This means a deepfake video or an audio-only phone interview with a voice spoof can sail through, especially if the interviewer isn’t aware of what to watch for.
The “human factor” is a weak link: hiring teams may doubt their instincts if something feels “off,” because it’s so novel to suspect a deepfake. As one CISO noted after encountering a suspicious interviewee, there were no established defenses or protocols—“defenses are still being written” for this scenario.
4. Siloed functions and rushing to hire.
Often, security teams are not involved in the hiring process; it’s viewed as HR’s domain. HR, for its part, may assume that standard checks (references, background screen) will catch any issues. This silo means no one is actively looking at the hiring pipeline through a security lens. Attackers count on this.
When a hiring manager urgently needs to fill a role, they may overlook small inconsistencies (e.g. a candidate’s video lag) in the interest of moving forward. Traditional workflows prioritize speed and candidate experience—not verification. Additionally, remote hiring processes instituted during COVID allowed for virtual document checks and lax verification that some companies have continued, creating an opening for fraud.
I-9 forms and work authorization are often handled on or after the first day of work; by that point, the “hire” is already in the building (literally or figuratively). If that person isn’t who they claimed, the company finds out far too late.
In summary, legacy hiring practices operate on an assumption of trust that no longer holds. They assume the person applying is who they say they are. They assume documents provided are genuine. They assume if someone passes an interview, they themselves did the work. Each of those assumptions has been upended by modern fraud techniques. CHROs and CISOs must recognize that without new controls, the hiring process is the soft underbelly of enterprise security
Organizational Risk: Compliance, Insider Threat, and Brand Damage
A successful candidate impersonation or deepfake hire doesn’t just bring in a “bad employee”—it introduces serious organizational risks across multiple dimensions:
Compliance and Legal Exposure
Hiring someone under false pretenses can put a company in violation of laws and regulations. In the extreme case of sanctioned nation-state operatives, companies have unknowingly breached U.S. sanctions laws—effectively doing business with a prohibited entity—which can result in hefty fines and legal action.
The North Korean IT worker schemes explicitly aim to evade international sanctions and channel funds to a hostile regime. Regulators are taking note; for instance, financial industry regulators have warned banks about this threat, and the U.S. Treasury has published advisories with red flags for fake identities in hiring.
Even beyond sanctions, there’s the issue of work authorization (e.g., Form I-9 in the US). If an employee used fake documents, the company could face penalties for improper employment eligibility verification. Compliance frameworks like SOC 2 and ISO 27001 also come into play—both emphasize controls around personnel security. For SOC 2, organizations must vet and authorize personnel who have access to systems and data. If someone slips through that vetting with a fake identity, it undermines those controls and could jeopardize compliance audits.
In highly regulated sectors (finance, healthcare, defense), an impostor could mean regulatory violations (imagine an unlicensed individual hired in healthcare, or a foreign national accessing export-controlled technology). In short, failing to catch fraudulent candidates can lead to legal liability, regulatory sanctions, or loss of certifications—a CISO’s and CHRO’s nightmare.

Insider Threat and Security Breach
From a security standpoint, a fraudulent hire is effectively the ultimate insider threat. You have granted an attacker a legitimate employee ID, email address, and network credentials. They can potentially bypass many security controls simply by virtue of being “on the inside.”
As Google’s cyber intel team put it, these individuals’ technical skill combined with their evasion tactics make them “particularly dangerous,” especially for HR and recruiting teams not equipped to spot threats during hiring. Once in, they can elevate privileges, install malware, or siphon data—all under the guise of an employee or contractor. We’ve already seen instances of data theft and extortion: North Korean hires have attempted to steal sensitive data from employers and later threatened to leak it unless paid ransom.
In other scenarios, an impostor could insert faulty code or backdoors into software (think of a developer with malicious intent). A CISO of a security firm noted that if a bad actor gets hired at a software provider and injects malware into the product, the company becomes a “super-spreader” of that malware to its customers. This is a nightmare scenario—a supply chain attack via a fake employee. Even if the fraudster’s aim is just to collect a paycheck, their incompetence or divided attention (if juggling multiple jobs) can introduce security lapses or errors. The insider risk is multifaceted: data breaches, financial fraud, sabotage, or simply an unreliable workforce member with access to critical systems.
Brand and Trust Damage
Beyond immediate legal and security impacts, there’s a reputational cost. If it becomes public that your organization was infiltrated by a fake candidate or a state-sponsored agent, the brand damage is significant. Customers and partners may lose trust—questioning your security maturity (“if you can’t even vet your staff, how can we trust you with our data?”).
Internally, it can shatter morale and trust in leadership. Boards and executives could face tough questions about oversight and due diligence. In some cases, companies have had to disclose incidents in financial filings or to regulators, drawing unwanted media attention. Consider also the trust within the team: other employees may feel unsettled knowing a colleague was an imposter, or angry if that person’s poor performance caused project failures. The hiring organization’s credibility takes a hit both externally and internally.
Proactively addressing this risk can conversely build brand trust—showing that your company takes innovative threats seriously and protects its people and customers. CHROs have a stake here too: HR is often the steward of company culture and employee experience. A major fraud incident in hiring is deeply disruptive to both.
In essence, the cost of a single fraudulent hire can far exceed a bad hire’s typical costs. It’s not just a hiring mistake; it’s a potential security incident, a compliance failure, and a PR fiasco wrapped into one. That’s why forward-looking organizations are treating hiring security as part of their enterprise risk management and insider threat programs—bridging the gap between HR and InfoSec priorities.
Building a Resilient Hiring Pipeline: Best Practices for Security & Trust
Mitigating these emerging risks requires rethinking and fortifying the hiring process end-to-end. The goal is to build a resilient hiring pipeline, one that can seamlessly verify candidate identities, detect fraud, and deter malicious actors, all while maintaining a good candidate experience and compliance. Here are best practices and strategies that CHROs and CISOs should consider jointly:
1. Introduce Identity Verification Steps into Hiring
Don’t rely on trust until the first day. At strategic points in the hiring funnel, incorporate an identity verification (IDV) checkpoint to confirm the candidate’s real identity. This could be early: for example, before a formal interview, ask the candidate to verify their government ID and a selfie through a secure portal.
Gartner recommends deploying ID verification “early in the recruiting process” to catch impersonators before too much time is invested. Some organizations choose to do it at the video interview stage or alongside skill assessments for high-assurance positions.
The key is to ensure the person you screen is the person you eventually hire, preventing the classic “bait-and-switch” where someone else shows up later. By verifying a candidate’s photo ID and matching it to a live selfie or live video, you can stop a deepfake or stand-in before they reach final rounds. This also deters fraud—honest candidates won’t mind an extra verification step when framed as a standard security policy, while fraudsters will likely drop out.
2. Strengthen Digital Background Checks and Credentialing
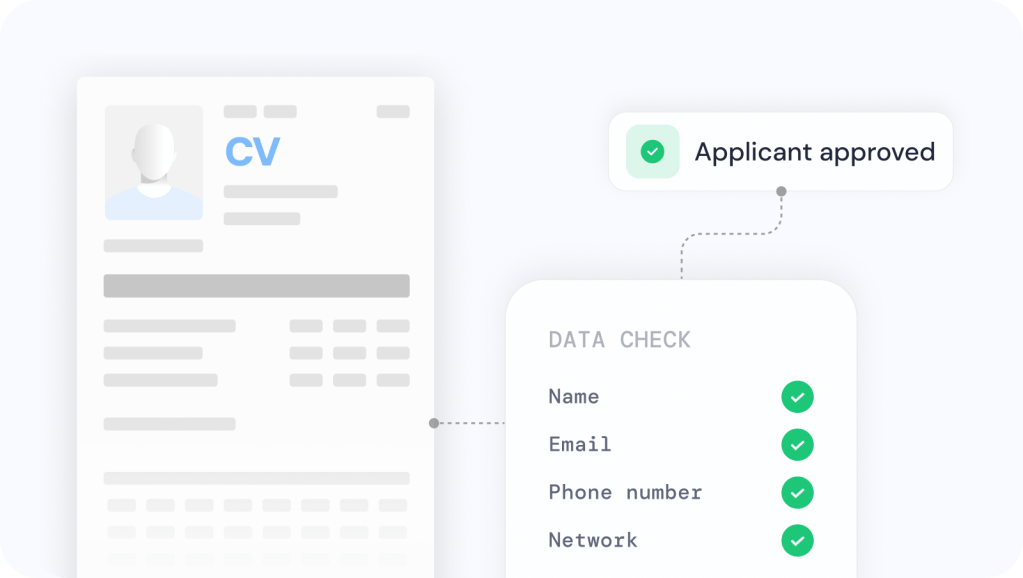
Go beyond the traditional background check. Leverage improved tools to vet the details candidates provide. For instance, use automated public records searches or professional record databases to confirm that the previous employers or universities on a resume actually exist and that the candidate was associated with them. Validate any professional licenses or certifications directly with issuing bodies. Conduct a quick open-source intelligence scan: does the person’s name, photo, and work history have a consistent presence online (in a non-fabricated way)?
HR teams should treat suspicious resumes with healthy skepticism, e.g., multiple overlaps or unverifiable companies could indicate a fraudulent profile. It’s also wise to perform a sanctions and watchlist screening on candidates in sensitive roles or from overseas, to catch any known bad actors (many background check services or identity platforms can automatically flag if an identity appears on government watchlists). Essentially, combine the power of data with the background check—checking not just “does this person have a criminal record?” but “does this identity make sense and match a real, consistent person?”.
A candidate verification layer can silently screen CVs by cross-referencing public data, records, and online presence to detect inconsistencies, fraud, or risk indicators before any contact is made.
3. Use In-Person or Live Confirmation for Key Stages
While not always feasible, having some form of live interaction that is hard to fake is invaluable. Requiring a short “camera-on” video call for finalists ensures you are interacting with a physical person and not a curated deep-fake video. Add a pre-join gate: many identity-verification platforms now integrate with Zoom, Teams, and Meet; a 3-second selfie + liveness check runs in the lobby (or immediately before encryption starts) so only the already-verified candidate can enter the meeting.
Train interviewers to include a bit of unscripted conversation—a prompt a deep-fake would struggle with due to lack of genuine spontaneity. One team exposed a fake candidate simply by asking, “Can you tell me about that picture on your wall?”
4. Secure the Onboarding Process
A resilient hiring pipeline extends into Day 1 and beyond. Coordinate with IT so that device provisioning, account creation, and IAM enrollment are tied to the same identity you verified during hiring.
At laptop pickup—or for remote hires, during a Day-1 video kickoff—repeat a quick selfie/ID match, mostly integrated within your identity provider workflows; this links the person receiving hardware or credentials to the vetted record. Ship devices only to verified addresses, or require in-person pickup at a trusted site; sudden address changes are a red flag.
Integrate identity verification processes into corporate IAM (Okta, Microsoft Entra, Ping, etc.) so the new account inherits a biometric or risk-based factor from the start. Conditional access can delay full network rights until that first login is confirmed. By baking identity assurance into onboarding and access control, you ensure that even if someone slipped through interviews, they must still prove they are the vetted individual when work actually begins—and any time they request an MFA/password reset, VPN token, or other sensitive action.
5. Cross-Functional Training and Awareness
The defense against hiring fraud is not purely technical—it’s also human vigilance. Provide training for recruiters and hiring managers on the common red flags of deepfakes and identity fraud. Teach HR staff what a deepfake glitch might look like (e.g. odd blinking, voice lag) and encourage them to pause and escalate if something seems off.
Foster a culture where HR can reach out to InfoSec for a second opinion on suspicious cases without stigma. Likewise, security teams should update their insider threat models to include scenarios of fraudulent hires. Organizations like Google suggest insider risk management should explicitly cover hiring risks, with clear policies and executive support . A cross-functional approach is crucial: Gartner emphasizes that recruiting alone can’t fight this—it requires IT, IAM, security, and legal collaborating. For example, involve the legal team early to design identity checks that comply with privacy laws and avoid discrimination.
Engage your compliance officers to map any new verification processes to relevant regulations (like making sure identity data from candidates is handled per GDPR/CCPA). When CHROs and CISOs jointly champion these efforts, it sends a message that hiring security is a company-wide priority, not a burden.
By implementing the above best practices, organizations can create multiple checkpoints that work in concert to thwart candidate fraud. The idea is not to make hiring an obstacle course for genuine candidates, but to intelligently add trust verifications that only the bad actors will struggle with. When designed well, these measures actually protect the candidate experience too, ensuring that honest applicants aren’t losing out to cheaters and that your workplace remains safe and merit-based.
Learn more about Incode Candidate Verification.
Incode was named a Leader in the 2025 Gartner® Magic Quadrant™ for Identity Verification. Download the report.
This is an excerpt from our e-book, “Securing the Hiring Process Against Deepfakes and Identity Fraud”, by Fernanda Sottil, Head of Workforce at Incode. Download your complimentary copy of our e-book, “Securing the Hiring Process Against Deepfakes and Identity Fraud”, to explore:
- The new threat surface: how hiring became a vector for attack
- The anatomy of a modern candidate fraud attempt
- Why traditional hiring processes are susceptible to fraud
- The risks organizations face in today’s talent landscape
- Best practices for building a resilient hiring pipeline
- Key criteria for evaluating a candidate verification solution
- Why leading enterprises trust Incode for identity assurance