Picture this: you’ve just hired a stellar remote developer. Their code is clean, they meet deadlines, and they seem like the perfect addition to your team.
Six months later, you discover they’re actually a North Korean operative who’s been siphoning your company’s data and funneling their salary to a sanctioned regime.
This isn’t science fiction. It’s happening right now through a sophisticated scheme called “laptop mules.”
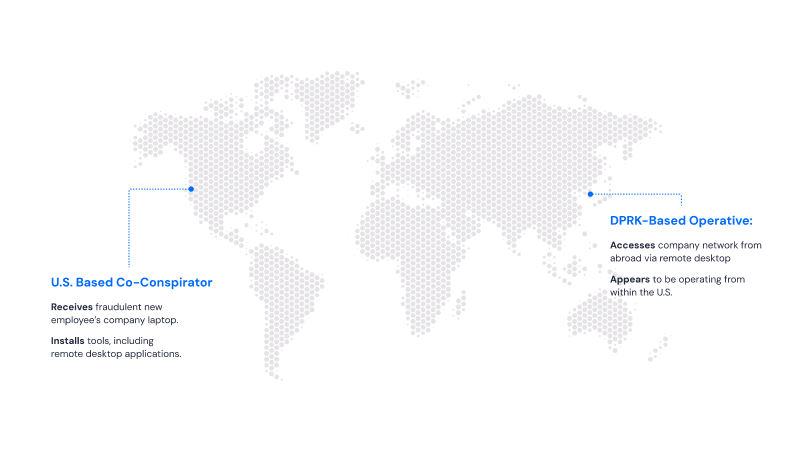
As remote work reshapes the global employment landscape, North Korean cyber operatives have found an ingenious way to exploit our hiring processes. By using local accomplices to receive and configure corporate laptops, they’re embedding state-sponsored agents within Western companies while appearing as legitimate remote employees.
This threat has prompted urgent warnings from federal agencies. The FBI’s Internet Crime Complaint Center issued Advisory I-012325-PSA in January 2025, specifically warning about “North Korean IT Workers Conducting Data Extortion.”
Similarly, the Cybersecurity and Infrastructure Security Agency (CISA) has elevated this to a national security priority, noting the direct connection to North Korea’s weapons programs.
The implications are staggering: sensitive data theft, financial losses, regulatory violations, and unwitting funding of sanctioned programs. Here’s the story of how this threat is unfolding and why every organization needs to understand it.
The KnowBe4 Incident: A Perfect Storm
In 2024, cybersecurity company KnowBe4 thought they had found the ideal remote software engineer. The candidate sailed through their rigorous interview process, passing technical screenings with flying colors. Their background check came back clean. Even their references checked out perfectly.
There was just one problem: the person didn’t exist.
KnowBe4 had actually hired a North Korean operative using a stolen U.S. citizen’s identity, complete with an AI-generated photograph that passed visual inspection. The fake employee had fooled experienced hiring managers, technical interviewers, and background verification systems.
The deception began to unravel almost immediately after the “employee” received their corporate MacBook. The operative immediately started to load malware on the device, but KnowBe4’s endpoint detection and response (EDR) software detected it and alerted their InfoSec Security Operations Center.
KnowBe4 CEO Stu Sjouwerman later revealed the timeline: “If it can happen to us, it can happen to almost anyone.” The company’s security team detected the suspicious activity within 25 minutes and contained the threat before any significant damage occurred.
Their HR team had conducted four video conference-based interviews on separate occasions, confirming the individual matched the AI-enhanced photo provided on their application.
The operative used a Raspberry Pi to download malware and attempted to manipulate session history files and execute unauthorized software. When the SOC team reached out to inquire about the anomalous activity, the fake employee claimed to be troubleshooting a router speed issue, but later became unresponsive.
How This Actually Happened: The Laptop Mule Playbook
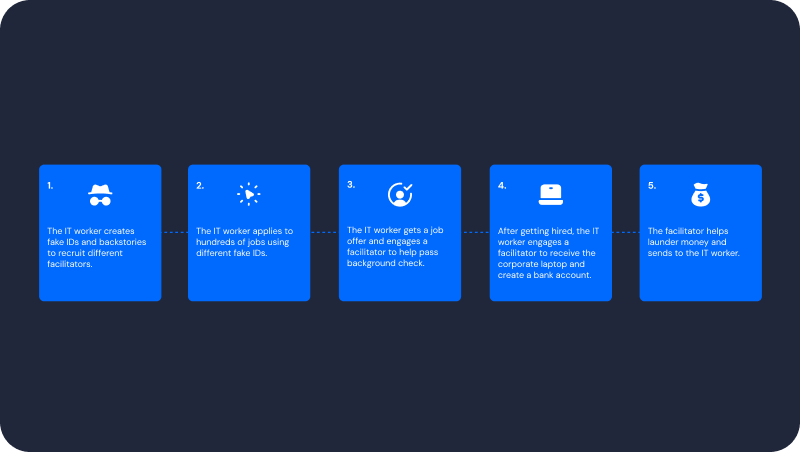
The KnowBe4 incident perfectly illustrates the six-phase laptop mule operation that North Korean operatives have refined into a repeatable playbook:
Phase 1: Identity Construction
The operative didn’t just steal a name. They crafted a complete digital persona using the victim’s legitimate Social Security number, fabricated work history, and professional references that could pass basic verification. Most sophisticated was the use of AI to generate a believable profile photograph that would pass video interview scrutiny.
Phase 2: The Interview Deception
Armed with technical skills and a convincing backstory, the operative applied for KnowBe4’s remote software engineering position. They demonstrated genuine coding abilities during technical screenings and maintained their cover throughout multiple interview rounds, using the AI-enhanced photograph to pass video verification.
Phase 3: Equipment Redirection
Once hired, the operative provided a shipping address that differed from their stated residence. This address led to what federal investigators call a “laptop mule” – a local accomplice who receives corporate equipment on behalf of foreign operatives.
Phase 4: Remote Configuration
The laptop mule configures the device so that the North Korean operative can VPN in from where they really physically are (North Korea or over the border in China) and work the night shift so that they seem to be working in US daytime. The device essentially becomes a portal into the corporate network, accessible from thousands of miles away.
Phase 5: The Failed Cover
The operative’s impatience proved to be their downfall. Instead of maintaining legitimate work patterns to build trust over time, they immediately began installing malware and attempting to access restricted systems. This aggressive approach triggered KnowBe4’s security monitoring within minutes.
Phase 6: The Larger Network
Post-incident investigation revealed this wasn’t an isolated attempt. The case was shared with Mandiant and the FBI, confirming it was part of a sophisticated state-sponsored operation targeting numerous companies simultaneously.
How Incode Stops Candidate Fraud
Incode brings real-time, adaptive identity verification to every stage of your recruiting workflow to protect and streamline the hiring process.
- Incode prevents fraudulent candidates from reaching the interview stage, helping reduce organizational risk, recruiting costs, and downstream disruption.
- Our platform not only blocks bad actors early, it also accelerates hiring with a seamless candidate experience that reduces manual review and enables faster, more confident decision-making.
- Adaptive biometric verification confirms each candidate’s real-world identity, giving recruiting teams confidence from initial application through Day 1 onboarding.
Learn more about how Incode’s Candidate Verification solution offers end-to-end protection from application to Day 1.
This Isn’t Isolated: A National Security Crisis
The KnowBe4 incident wasn’t a one-off attempt by a lone actor. It was part of a massive, coordinated campaign that federal investigators have been tracking across hundreds of companies.
Stay tuned for part 2, in which we expose more real-life examples of North Korean infiltration operations.
Additional Resources
- FBI Internet Crime Complaint Center – North Korean IT Workers Conducting Data Extortion (January 2025)
- FBI Internet Crime Complaint Center – DPRK IT Workers Defrauding U.S. Businesses (May 2024)
- KnowBe4 Official Blog – How a North Korean Fake IT Worker Tried to Infiltrate Us
- FBI DPRK IT Workers Wanted Page
- Department of Justice – Matthew Isaac Knoot Nashville Case (August 2024)
- Department of Justice – Christina Chapman Arizona Case (February 2025)
- Department of Justice – Fourteen North Korean Nationals Indicted (February 2025)
Author

Carrie Melanda is a Product Marketing Manager at Incode. She brings deep expertise in product marketing and go-to-market strategy, with a proven track record of driving revenue growth and market differentiation in the cybersecurity space.