Platform
Everything in one place
No-code flow builder
Brand-aligned journeys
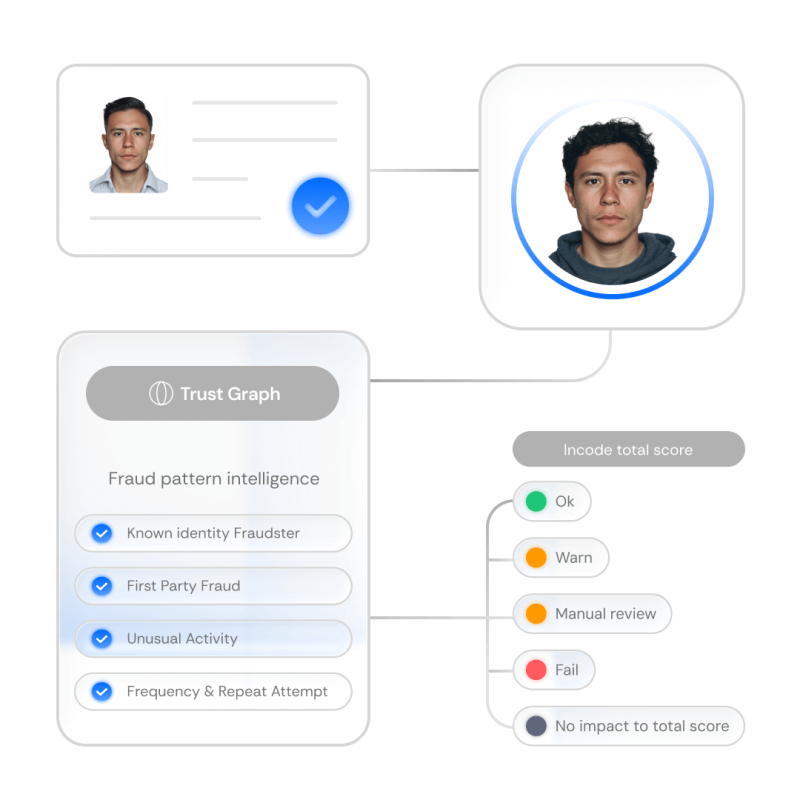
Transparency on every session
Monitor performance and trends
Smarter case reviews
APIs and SDKs
Featured Modules
Platform
Platform
Everything in one place
No-code flow builder
Brand-aligned journeys
Transparency on every session
Monitor performance and trends
Smarter case reviews
APIs and SDKs
Featured Products
Featured Modules
Solutions
Resources
Learning
For developers